Information security
VXG follows best practices in Information Security (IS). All the software is developed internally and services are provided by VXG employees. All employees are in Ontario, Canada. VXG maintains internal IS policies and documentation such as:
VXG Data Protection Policy.
VXG Information Security Policy.
VXG Software Development Guidelines.
The documents are available upon request. VXG conducts periodic reviews of IS and training for its employees.
Remote access
VXG provides managed services for the Cloud VMS deployed on customers’ infrastructure. The is granted and fully controlled by a customer.
In the case of AWS deployments, it is managed by IAM (Identity and Access Management). Each VXG employee will have their own credentials and every access will be logged in the system.
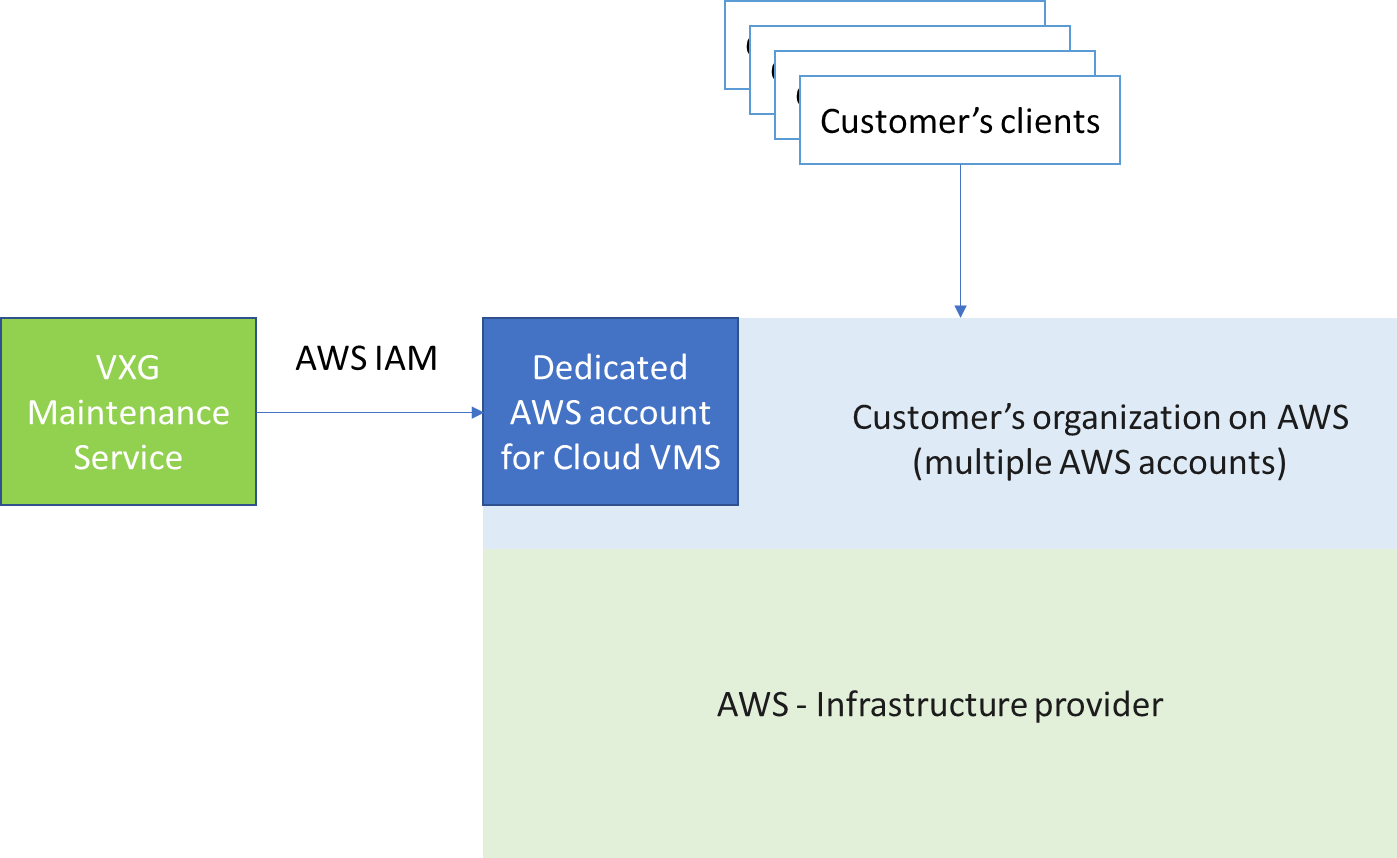
In the case of AWS, we recommend creating a brand new account and adding it to your organization at AWS. VXG will only have access to this isolated account dedicated to Cloud VMS.